Cybersecurity teams from Microsoft on Saturday disclosed they recognized proof of a new destructive malware operation focusing on governing administration, non-earnings, and data technology entities in Ukraine amid brewing geopolitical tensions concerning the nation and Russia.
“The malware is disguised as ransomware but, if activated by the attacker, would render the infected laptop process inoperable,” Tom Burt, company vice president of buyer security and have faith in at Microsoft, said, including the intrusions have been aimed at authorities companies that supply critical government branch or unexpected emergency reaction functions.
Also focused is an IT company that “manages sites for public and non-public sector purchasers, together with govt organizations whose web sites had been not long ago defaced,” Burt mentioned.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

The computing big, which initial detected the malware on January 13, attributed the attacks to an emerging threat cluster codenamed “DEV-0586,” with no noticed overlaps in methods and treatments to other formerly documented groups. It further said the malware was observed on dozens of impacted techniques, a quantity it expects to enhance as the investigation proceeds.
According to Microsoft Threat Intelligence Centre (MSTIC) and Microsoft Digital Security Device (DSU), the attack chain is a two-phase process that entails —
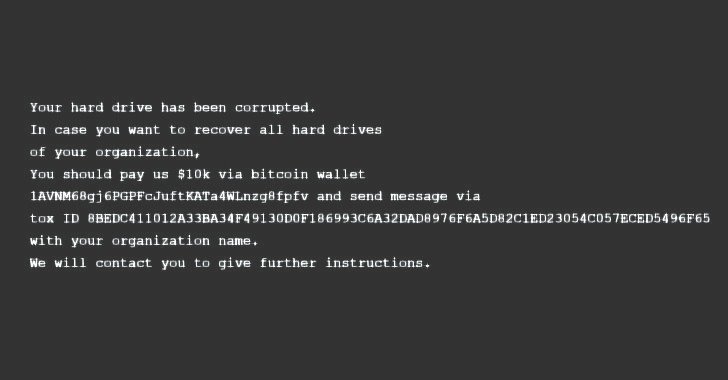
- Overwriting the Master Boot History (MBR), the first sector of any tough disk that identifies where the working system is located in the disk so that it can be loaded into a computer’s RAM, on a victim’s procedure to screen a bogus ransom observe urging the focus on to shell out an amount of money of $10,000 to a bitcoin wallet
- A 2nd-stage executable that retrieves a file corrupter malware hosted on a Discord channel that’s built to lookup for information with 189 distinctive extensions, then irrevocably overwrite their contents with a mounted range of 0xCC bytes and rename just about every file with a seemingly random four-byte extension.
The malicious activity is “inconsistent” with cybercriminal ransomware exercise for good reasons that “explicit payment quantities and cryptocurrency wallet addresses are hardly ever specified in present day felony ransom notes” and “the ransom observe in this scenario does not involve a custom made ID,” Microsoft explained.
The improvement arrives as quite a few governing administration internet websites in the Eastern European region have been defaced on Friday with a information warning Ukrainians that their personal facts was becoming uploaded to the Internet. The Security Provider of Ukraine (SSU) mentioned it uncovered “indications” of involvement of hacking teams related with the Russian intelligence companies.
“Provided the scale of the noticed intrusions, MSTIC is not capable to evaluate intent of the recognized destructive actions but does think these actions depict an elevated risk to any federal government agency, non-profit or company positioned or with units in Ukraine,” the researchers cautioned.
Having said that, Reuters previously these days raised the possibility that the attacks might have been the get the job done of an espionage group linked to Belarusian intelligence which is tracked as UNC1151 and Ghostwriter. “Several substantial intrusions into Ukrainian govt entities have been executed by UNC1151,” cybersecurity firm Mandiant disclosed in a report in November 2021, pointing out the group’s operations as people aligned with Belarusian federal government passions.
Found this posting exciting? Stick to THN on Fb, Twitter and LinkedIn to study more exceptional content material we publish.
Some components of this post are sourced from:
thehackernews.com


 Russia Arrests REvil Ransomware Gang Responsible for High-Profile Cyber Attacks
Russia Arrests REvil Ransomware Gang Responsible for High-Profile Cyber Attacks