The Russia-connected APT29 country-point out actor has been discovered leveraging a “lesser-acknowledged” Windows element referred to as Credential Roaming as portion of its attack in opposition to an unnamed European diplomatic entity.
“The diplomatic-centric concentrating on is constant with Russian strategic priorities as perfectly as historic APT29 targeting,” Mandiant researcher Thibault Van Geluwe de Berlaere said in a technological generate-up.
APT29, a Russian espionage group also known as Cozy Bear, Iron Hemlock, and The Dukes, is known for its intrusions aimed at collecting intelligence that align with the country’s strategic targets. It is considered to be sponsored by the International Intelligence Services (SVR).

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Some of the adversarial collective’s cyber routines are tracked publicly under the moniker Nobelium, a menace cluster responsible for the popular provide chain compromise by means of SolarWinds software package in December 2020.
The Google-owned danger intelligence and incident response agency claimed it recognized the use of Credential Roaming throughout the time APT29 was present inside the target network in early 2022, at which place “quite a few LDAP queries with atypical attributes” were being carried out against the Lively Listing procedure.
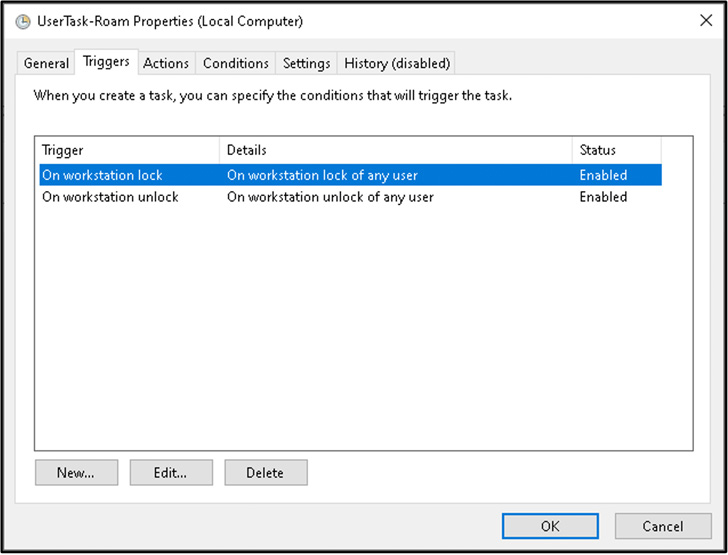
Released in Windows Server 2003 Support Pack 1 (SP1), Credential Roaming is a system that enables users to accessibility their credentials (i.e., non-public keys and certificates) in a protected fashion across diverse workstations in a Windows domain.
Investigating its interior workings even further, Mandiant highlighted the discovery of an arbitrary file write vulnerability that could be weaponized by a threat actor to attain remote code execution in the context of the logged-in victim.

The shortcoming, tracked as CVE-2022-30170, was addressed by Microsoft as element of Patch Tuesday updates transported on September 13, 2022, with the enterprise emphasizing that exploitation demands a consumer to log in to Windows.
“An attacker who efficiently exploited the vulnerability could obtain distant interactive logon legal rights to a device exactly where the victim’s account would not typically hold such privilege,” it famous.
Mandiant explained the research “offers insight into why APT29 is actively querying the similar LDAP attributes in Active Directory,” urging companies to utilize the September 2022 patches to protected against the flaw.
Discovered this report interesting? Adhere to THN on Facebook, Twitter and LinkedIn to go through more distinctive articles we article.
Some parts of this short article are sourced from:
thehackernews.com

 Several Cyber Attacks Observed Leveraging IPFS Decentralized Network
Several Cyber Attacks Observed Leveraging IPFS Decentralized Network