Citrix has issued an emergency advisory warning its prospects of a security issue impacting its NetScaler application supply controller (ADC) devices that attackers are abusing to launch amplified distributed denial-of-service (DDoS) attacks towards a number of targets.
“An attacker or bots can overwhelm the Citrix ADC [Datagram Transport Layer Security] network throughput, potentially leading to outbound bandwidth exhaustion,” the organization observed. “The impact of this attack appears to be extra distinguished on connections with constrained bandwidth.”
ADCs are objective-crafted networking appliances whose function is to enhance the performance, security, and availability of programs sent above the web to end-buyers.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The desktop virtualization and networking assistance supplier claimed it really is checking the incident and is continuing to investigate its effect on Citrix ADC, introducing “the attack is restricted to a compact number of buyers all-around the environment.”
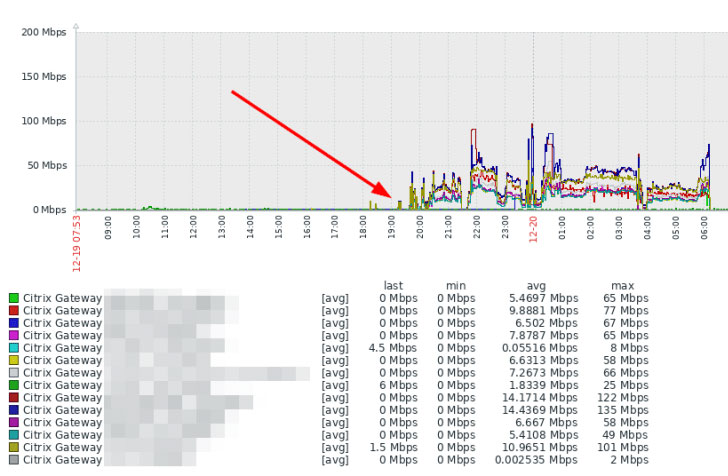
The issue arrived to gentle right after a number of stories of a DDoS amplify attack over UDP/443 towards Citrix (NetScaler) Gateway units at the very least considering that December 19, in accordance to Marco Hofmann, an IT administrator for a German computer software business ANAXCO GmbH.
Datagram Transportation Layer Security or DTLS is dependent on the Transportation Layer Security (TLS) protocol that aims to provide secure communications in a way that is created to thwart protect against eavesdropping, tampering, or information forgery.
Because DTLS utilizes the connectionless Consumer Datagram Protocol (UDP) protocol, it is really simple for an attacker to spoof an IP packet datagram and include an arbitrary supply IP address.
Thus when the Citrix ADC is flooded with an overpowering flux of DTLS packets whose source IP addresses are solid to a victim IP tackle, the elicit responses lead to an oversaturation of bandwidth, developing a DDoS condition.
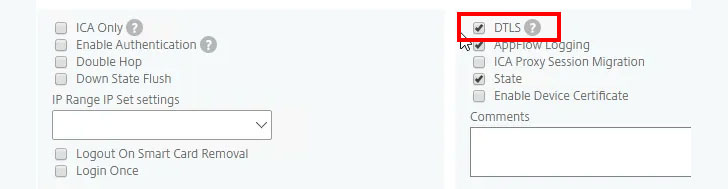
Citrix is at the moment operating to enrich DTLS to get rid of the susceptibility to this attack, with an envisioned patch to be produced on January 12, 2021.
To identify if a Citrix ADC devices is qualified by the attack, Cisco endorses preserving an eye on the outbound traffic volume for any important anomaly or spikes.
Clients impacted by the attack, in the meantime, can disable DTLS although a permanent fix from Citrix is pending by managing the next command on the Citrix ADC: “set vpn vserver
Discovered this article exciting? Observe THN on Facebook, Twitter and LinkedIn to examine a lot more exceptional articles we article.
Some sections of this short article are sourced from:
thehackernews.com


 Hacker Earns $2m in Bug Bounties
Hacker Earns $2m in Bug Bounties