Cybersecurity researchers have disclosed a new variant of the AvosLocker ransomware that disables antivirus options to evade detection right after breaching target networks by taking gain of unpatched security flaws.
“This is the to start with sample we observed from the U.S. with the ability to disable a protection alternative applying a genuine Avast Anti-Rootkit Driver file (asWarPot.sys),” Development Micro researchers, Christoper Ordonez and Alvin Nieto, said in a Monday examination.
“In addition, the ransomware is also able of scanning numerous endpoints for the Log4j vulnerability (Log4shell) utilizing Nmap NSE script.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
AvosLocker, one of the newer ransomware households to fill the vacuum remaining by REvil, has been linked to a quantity of attacks that focused critical infrastructure in the U.S., such as money companies and federal government facilities.
A ransomware-as-a-services (RaaS) affiliate-dependent group initially spotted in July 2021, AvosLocker goes over and above double extortion by auctioning data stolen from victims must the qualified entities refuse to shell out the ransom.
Other targeted victims claimed by the ransomware cartel are claimed to be found in Syria, Saudi Arabia, Germany, Spain, Belgium, Turkey, the U.A.E., the U.K., Canada, China, and Taiwan, according to an advisory released by the U.S. Federal Bureau of Investigation (FBI) in March 2022.
Telemetry facts gathered by Trend Micro shows that the meals and beverage sector was the most strike sector concerning July 1, 2021 and February 28, 2022, adopted by technology, finance, telecom, and media verticals.
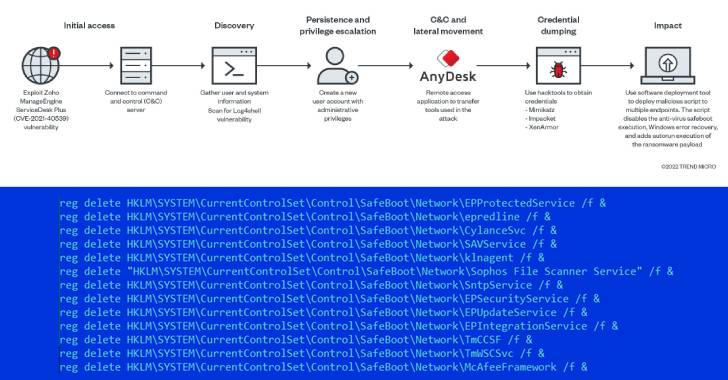
The entry issue for the attack is considered to have been facilitated by leveraging an exploit for a distant code execution flaw in Zoho’s ManageEngine ADSelfService Furthermore software package (CVE-2021-40539) to run an HTML software (HTA) hosted on a remote server.
“The HTA executed an obfuscated PowerShell script that incorporates a shellcode, capable of connecting again to the [command-and-control] server to execute arbitrary commands,” the researchers described.

This consists of retrieving an ASPX web shell from the server as effectively as an installer for the AnyDesk distant desktop software, the latter of which is utilised to deploy supplemental equipment to scan the community network, terminate security application, and fall the ransomware payload.
Some of the parts copied to the infected endpoint are a Nmap script to scan the network for the Log4Shell remote code execution flaw (CVE-2021-44228) and a mass deployment device termed PDQ to deliver a malicious batch script to many endpoints.
The batch script, for its section, is geared up with a broad vary of abilities that allows it to disable Windows Update, Windows Defender, and Windows Error Restoration, in addition to preventing safe boot execution of security merchandise, developing a new admin account, and launching the ransomware binary.
Also employed is aswArPot.sys, a legitimate Avast anti-rootkit driver, to destroy procedures connected with various security solutions by weaponizing a now-mounted vulnerability in the driver the Czech enterprise settled in June 2021.
“The final decision to choose the precise rootkit driver file is for its functionality to execute in kernel manner (as a result working at a superior privilege),” the researchers pointed out. “This variant is also capable of modifying other specifics of the put in security solutions, this kind of as disabling the lawful observe.”
Observed this report interesting? Abide by THN on Fb, Twitter and LinkedIn to examine a lot more distinctive content we put up.
Some sections of this short article are sourced from:
thehackernews.com

 Chinese Hackers Caught Exploiting Popular Antivirus Products to Target Telecom Sector
Chinese Hackers Caught Exploiting Popular Antivirus Products to Target Telecom Sector