Trojanized installers of the Telegram messaging application are remaining used to distribute the Windows-based mostly Purple Fox backdoor on compromised units.
That’s according to new research revealed by Minerva Labs, describing the attack as different from intrusions that generally choose benefit of respectable software program for dropping malicious payloads.
“This threat actor was capable to leave most parts of the attack beneath the radar by separating the attack into numerous smaller documents, most of which had very reduced detection fees by [antivirus] engines, with the final phase leading to Purple Fox rootkit an infection,” researcher Natalie Zargarov stated.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Initially discovered in 2018, Purple Fox will come with rootkit capabilities that allow for the malware to be planted beyond the get to of security remedies and evade detection. A March 2021 report from Guardicore in-depth its worm-like propagation attribute, enabling the backdoor to spread a lot more quickly.

Then in October 2021, Development Micro scientists uncovered a .NET implant dubbed FoxSocket deployed in conjunction with Purple Fox that normally takes gain of WebSockets to call its command-and-control (C2) servers for a additional safe indicates of developing communications.
“The rootkit abilities of Purple Fox make it far more able of carrying out its objectives in a stealthier fashion,” the scientists mentioned. “They allow Purple Fox to persist on impacted units as nicely as produce even more payloads to affected devices.”
Very last but not the very least, in December 2021, Trend Micro also lose mild on the later levels of the Purple Fox an infection chain, focusing on SQL databases by inserting a destructive SQL common language runtime (CLR) module to attain a persistent and stealthier execution and ultimately abuse the SQL servers for illicit cryptocurrency mining.
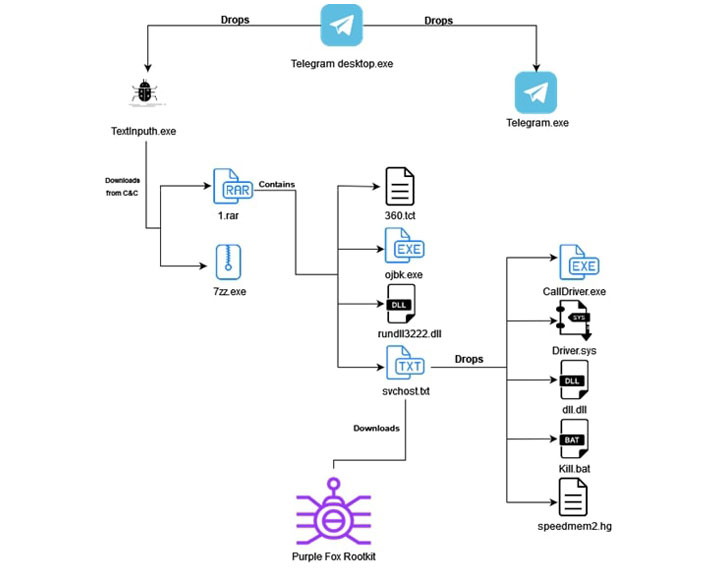
The new attack chain observed by Minerva commences with a Telegram installer file, an AutoIt script that drops a authentic installer for the chat app and a destructive downloader called “TextInputh.exe,” the latter of which is executed to retrieve future-stage malware from the C2 server.
Subsequently, the downloaded information continue to block processes associated with diverse antivirus engines, before advancing to the ultimate phase that results in the down load and execution of the Purple Fox rootkit from a now-shut down remote server.
“We located a massive amount of destructive installers delivering the exact Purple Fox rootkit variation making use of the identical attack chain,” Zargarov claimed. “It looks like some were shipped by using email, although other folks we presume ended up downloaded from phishing websites. The splendor of this attack is that each individual stage is divided to a various file which are ineffective with out the total file established.”
Identified this write-up attention-grabbing? Observe THN on Fb, Twitter and LinkedIn to study extra unique written content we article.
Some parts of this posting are sourced from:
thehackernews.com



 Detecting Evasive Malware on IoT Devices Using Electromagnetic Emanations
Detecting Evasive Malware on IoT Devices Using Electromagnetic Emanations