U.S. cybersecurity and intelligence organizations have posted a joint advisory warning of attacks perpetrated by a cybercrime gang recognised as the Daixin Workforce mainly concentrating on the healthcare sector in the nation.
“The Daixin Team is a ransomware and data extortion team that has qualified the HPH Sector with ransomware and details extortion operations considering that at minimum June 2022,” the companies explained.
The alert was posted Friday by the Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), and the Section of Well being and Human Products and services (HHS).

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Above the previous four months, the team has been joined to many ransomware incidents in the Healthcare and Community Well being (HPH) sector, encrypting servers similar to electronic overall health information, diagnostics, imaging, and intranet companies.
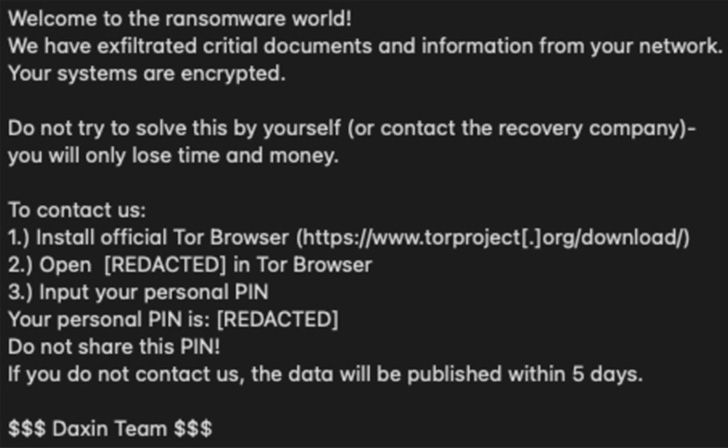
It really is also mentioned to have exfiltrated particular identifiable data (PII) and individual health and fitness facts (PHI) as component of a double extortion scheme to secure ransoms from victims.
A single of those attacks was aimed at OakBend Clinical Centre on September 1, 2022, with the group boasting to have siphoned around 3.5GB of information, which includes above just one million data with individual and employee information and facts.
It also released a sample that contains 2,000 client documents on its info leak site, which incorporated names, genders, dates of beginning, Social Security numbers, addresses, and other appointment aspects, according to DataBreaches.net.
On Oct 11, 2022, it notified its buyers of emails despatched by “third-functions” regarding the cyber attack, stating it is specifically informing affected clients, in addition to featuring absolutely free credit monitoring services for 18 months.
Per the new alert, initial access to focused networks is attained by usually means of digital non-public network (VPN) servers, usually getting benefit of unpatched security flaws and compromised qualifications acquired by means of phishing e-mails.

On getting a foothold, the Daixin Crew has been observed moving laterally by producing use of remote desktop protocol (RDP) and protected shell (SSH), adopted by attaining elevated privileges working with techniques like credential dumping.
“The actors have leveraged privileged accounts to get access to VMware vCenter Server and reset account passwords for ESXi servers in the setting,” the U.S. govt explained. “The actors have then employed SSH to connect to accessible ESXi servers and deploy ransomware on these servers.”
What’s additional, the Daixin Team’s ransomware is based mostly on an additional pressure known as Babuk that was leaked in September 2021, and has been employed as a basis for a number of file-encrypting malware households these types of as Rook, Evening Sky, Pandora, and Cheerscrypt.
As mitigations, it can be suggested that businesses implement the newest software package updates, implement multi-factor authentication, carry out network segmentation, and retain periodic offline backups.
Found this report fascinating? Comply with THN on Fb, Twitter and LinkedIn to examine much more unique content material we publish.
Some components of this write-up are sourced from:
thehackernews.com


 Why Ransomware in Education on the Rise and What That Means for 2023
Why Ransomware in Education on the Rise and What That Means for 2023