A crimeware-similar menace actor identified as Haskers Gang has unveiled an information-stealing malware known as ZingoStealer for absolutely free on, allowing for other legal teams to leverage the tool for nefarious applications.
“It attributes the capability to steal delicate info from victims and can down load further malware to contaminated units,” Cisco Talos scientists Edmund Brumaghin and Vanja Svajcer explained in a report shared with The Hacker News.
“In quite a few conditions, this consists of the RedLine Stealer and an XMRig-based mostly cryptocurrency mining malware that is internally referred to as ‘ZingoMiner.'”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
But in an interesting twist, the criminal team announced on Thursday that the ownership of the ZingoStealer undertaking is changing hands to a new danger actor, in addition to presenting to market the resource code for a negotiable selling price of $500.
Since its inception very last month, ZingoStealer is reported to be going through reliable advancement and deployed specifically versus Russian-speaking victims by packaging it as activity cheats and pirated software program. Haskers Gang is recognised to be lively because at the very least January 2020.
Besides harvesting sensitive details these as qualifications, thieving cryptocurrency wallet information, and mining cryptocurrency on victims’ systems, the malware leverages Telegram as both an exfiltration channel as perfectly as a platform to distribute updates.

Consumers of the merchandise can choose to pay about $3 to encase the malware in a custom crypter identified as ExoCrypt that can make it probable to evade antivirus defenses with no possessing to count on a 3rd-party crypter option.
The incorporation of the XMRig cryptocurrency mining software package into the stealer, the researchers claimed, is an attempt on the element of the malware author to further monetize their initiatives by making use of techniques infected by affiliate marketers to produce Monero cash.
Malicious campaigns offering the malware take the sort of a sport modification utility or a application crack, with the risk actors submitting YouTube films advertising the tools’ capabilities and its description, like a website link to an archive file hosted on Google Generate or Mega that has the ZingoStealer payload.

That claimed, Cisco Talos pointed out that the executables are also getting hosted on the Discord CDN, increasing the risk that the infostealer is staying disseminated inside gaming-similar Discord servers.
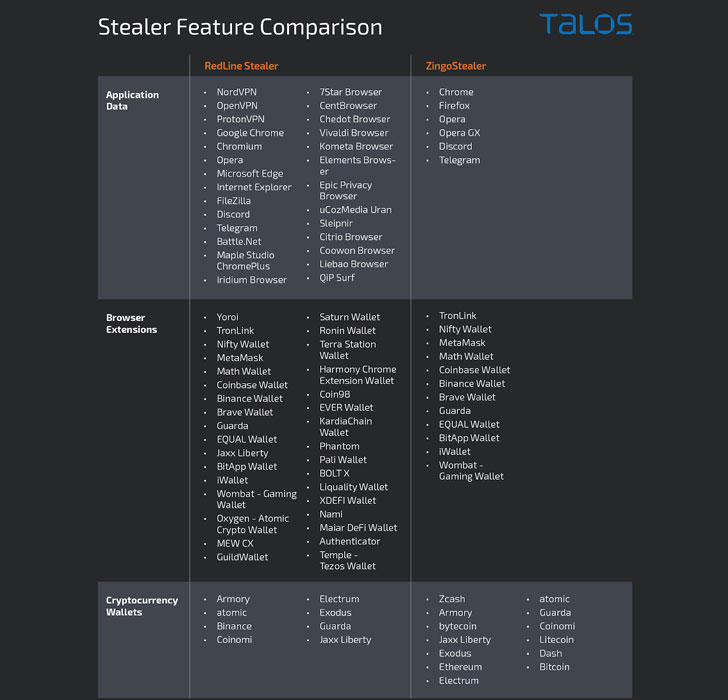
ZingoStealer, for its section, is fashioned as a .NET binary that is able of gathering procedure metadata and data saved by web browsers these as Google Chrome, Mozilla Firefox, Opera, and Opera GX, even though also siphoning information from cryptocurrency wallets.
What’s much more, the malware is outfitted to deploy secondary malware at the discretion of the attacker, these kinds of as RedLine Stealer, a additional function-rich details stealer that plunders knowledge from many applications, browsers, and cryptocurrency wallets and extensions. This possibly might demonstrate why the malware authors are giving ZingoStealer for no cost to any adversary.
“Buyers should be mindful of the threats posed by these sorts of apps and need to make certain that they are only executing purposes distributed through respectable mechanisms,” the scientists explained.
Located this posting fascinating? Observe THN on Fb, Twitter and LinkedIn to browse far more exclusive content material we post.
Some pieces of this write-up are sourced from:
thehackernews.com



 Critical Auth Bypass Bug Reported in Cisco Wireless LAN Controller Software
Critical Auth Bypass Bug Reported in Cisco Wireless LAN Controller Software