Many Windows machines situated in South Korea have been focused by a botnet tracked as PseudoManuscrypt considering the fact that at the very least Might 2021 by utilizing the same shipping methods of one more malware named CryptBot.
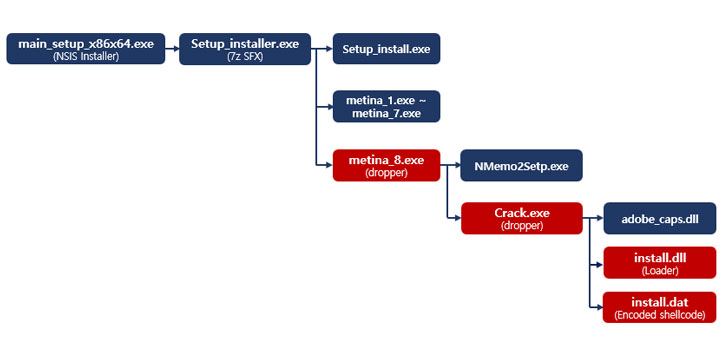
“PseudoManuscrypt is disguised as an installer that is equivalent to a sort of CryptBot, and is being distributed,” South Korean cybersecurity business AhnLab Security Crisis Reaction Centre (ASEC) claimed in a report revealed now.
“Not only is its file variety very similar to CryptBot, but it is also dispersed by using malicious web sites uncovered on the best research web site when customers look for industrial computer software-similar illegal systems these as Crack and Keygen,” it extra.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
According to ASEC, all over 30 personal computers in the state are being regularly infected on a daily basis on regular.
PseudoManuscrypt was initial documented by Russian cybersecurity firm Kaspersky in December 2021, when it disclosed details of a “mass-scale adware attack campaign” infecting much more than 35,000 computers in 195 nations around the world globally.
Targets of PseudoManuscrypt attacks, which it at first uncovered in June 2021, consist of a substantial amount of industrial and authorities businesses, which includes enterprises in the military-industrial elaborate and analysis laboratories, in Russia, India, and Brazil, amongst many others.
The principal payload module is equipped with comprehensive and diverse spying operation that provides the attackers with nearly full management of the infected program. It features stealing VPN connection facts, recording audio with the microphone, and capturing clipboard contents and running program function log facts.
Furthermore, PseudoManuscrypt can access a distant command-and-command server underneath the attacker’s command to have out a variety of nefarious functions these kinds of as file down load, execute arbitrary commands, log keypresses, and capture screenshots and films of the monitor.
“As this malware is disguised as an illegal computer software installer and is distributed to random men and women by using destructive web-sites, people need to be cautious not to download related programs,” the researchers claimed. “As destructive documents can also be registered to provider and execute continual malicious behaviors with out the user being aware of, periodic Personal computer upkeep is essential.”
Observed this posting attention-grabbing? Abide by THN on Fb, Twitter and LinkedIn to examine more unique articles we article.
Some elements of this write-up are sourced from:
thehackernews.com



 NordPass teams up with insurance provider Cowbell Cyber to improve security awareness
NordPass teams up with insurance provider Cowbell Cyber to improve security awareness