As ransomware attacks towards critical infrastructure skyrocket, new research demonstrates that threat actors guiding such disruptions are ever more shifting from working with email messages as an intrusion route to obtaining accessibility from cybercriminal enterprises that have presently infiltrated significant targets.
“Ransomware operators normally get entry from independent cybercriminal teams who infiltrate important targets and then offer accessibility to the ransomware actors for a slice of the unwell-gotten gains,” researchers from Proofpoint mentioned in a create-up shared with The Hacker News.
“Cybercriminal menace groups previously distributing banking malware or other trojans may perhaps also grow to be portion of a ransomware affiliate network.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
In addition to angling for a piece of the unlawful profits, the email and cloud security agency mentioned it is at this time tracking at the very least 10 diverse danger actors who engage in the function of “original access facilitators” to offer affiliates and other cybercrime groups with an entry level to deploy data theft and encryption functions.

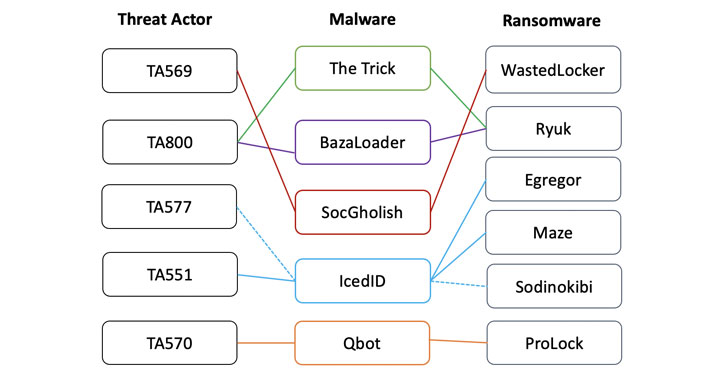
Initial entry brokers are recognized to infiltrate the networks by using very first-stage malware payloads this sort of as The Trick, Dridex, Qbot, IcedID, BazaLoader, or Buer Loader, with most strategies detected in the 1st 50 % of 2021 leveraging banking trojans as ransomware loaders.
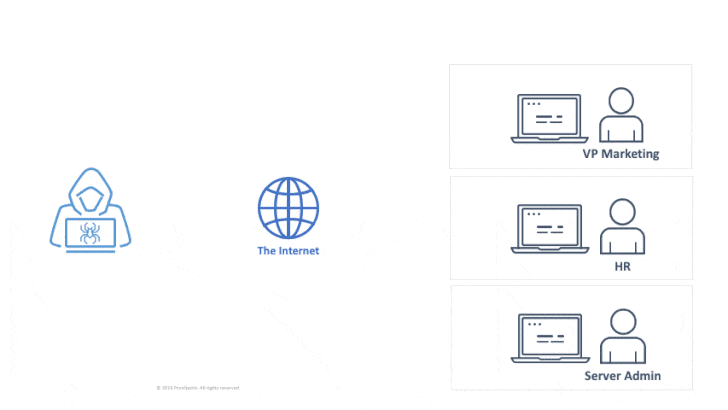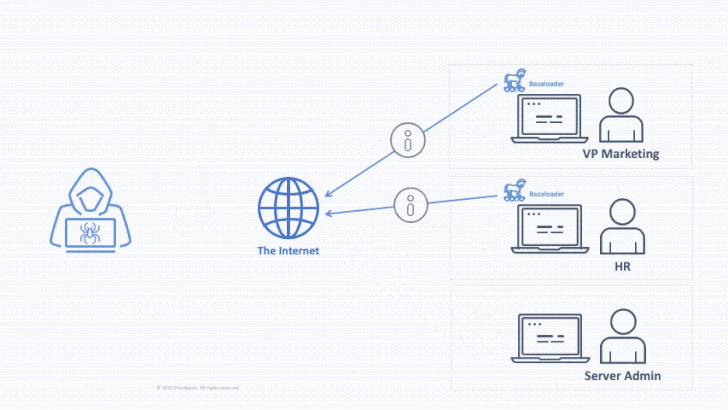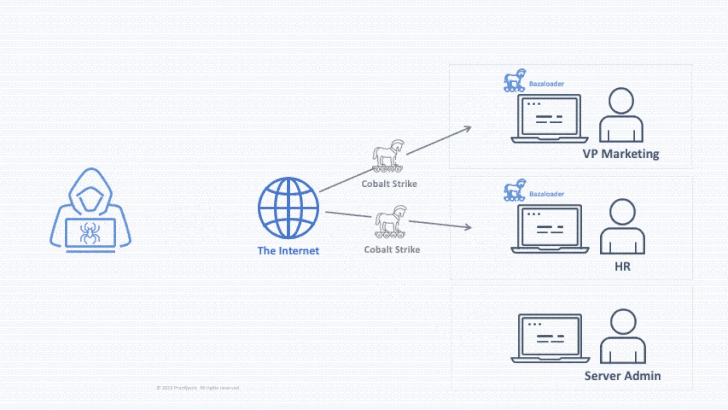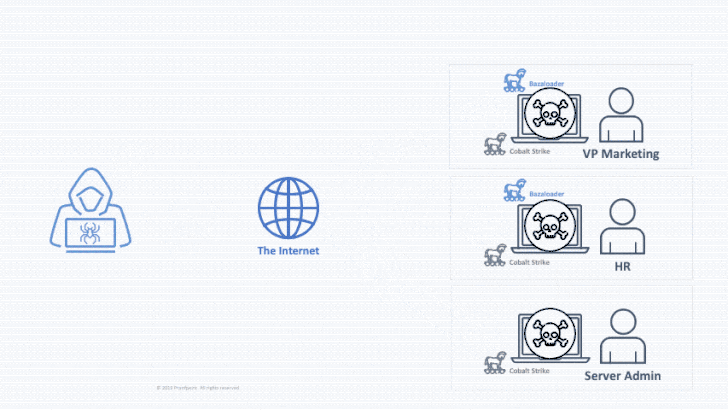
The brokers — which were recognized by tracking the backdoor access advertised on hacking message boards — incorporate TA800, TA577, TA569, TA551 (Shathak), TA570, TA547, TA544 (Bamboo Spider), TA571, TA574, and TA575, with overlaps observed among many menace actors, malware, and ransomware deployments.

For case in point, each TA577 and TA551 have been discovered to use IcedID as an preliminary entry payload to supply Egregor, Maze, and REvil ransomware, even though TA800 has employed BazaLoader to deploy Ryuk on qualified techniques.
In a hypothetical attack chain, a danger actor could mail an email with a malware-contaminated Office doc, which, when opened, drops the first-phase payload to maintain persistent backdoor entry. This entry can then be bought to a next threat actor, who exploits it to deploy a Cobalt Strike beacon to pivot throughout the broader network and deploy the ransomware laterally.
That mentioned, attacks that count on email messages to instantly distribute ransomware in the variety of malicious attachments or embedded hyperlinks proceed to continue being a threat, albeit at decrease volumes. Proofpoint pointed out that it discovered 54 ransomware campaigns distributing a minor around just one million messages around the earlier calendar year.
“Shorter dwell moments, high payouts, and collaboration throughout cybercriminal ecosystems have led to a great storm of cybercrime that the world’s governments are getting very seriously,” the researchers concluded. “It is possible with new disruptive attempts focused on the threat and escalating investments in cyber defense throughout offer chains, ransomware attacks will minimize in frequency and efficacy.”
Observed this posting fascinating? Follow THN on Facebook, Twitter and LinkedIn to browse extra unique written content we write-up.
Some parts of this short article are sourced from:
thehackernews.com

 Critical ThroughTek Flaw Opens Millions of Connected Cameras to Eavesdropping
Critical ThroughTek Flaw Opens Millions of Connected Cameras to Eavesdropping