Cybersecurity researchers have uncovered even more links concerning BlackCat (aka AlphaV) and BlackMatter ransomware families, the former of which emerged as a substitute subsequent international scrutiny past calendar year.
“At the very least some users of the new BlackCat group have links to the BlackMatter group, since they modified and reused a personalized exfiltration tool […] and which has only been noticed in BlackMatter exercise,” Kaspersky scientists claimed in a new evaluation.
The tool, dubbed Fendr, has not only been upgraded to incorporate extra file kinds but also applied by the gang extensively to steal info from corporate networks in December 2021 and January 2022 prior to encryption, in a well-liked tactic referred to as double extortion.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The conclusions appear less than a month following Cisco Talos scientists identified overlaps in the ways, approaches, and treatments (TTPs) in between BlackCat and BlackMatter, describing the new ransomware variant as a situation of “vertical small business enlargement.”
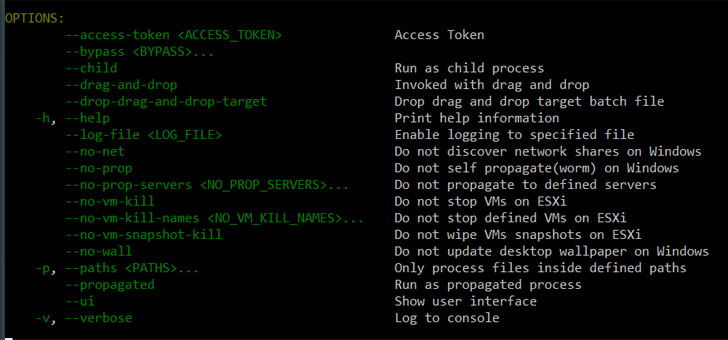
BlackCat stands out for two good reasons: it is an affiliate actor that has deployed BlackMatter in the previous and its malware is published in Rust, indicating how danger actors are more and more pivoting to programming languages with cross-compilation capabilities.
The group “delivers infrastructure, malware samples, ransom negotiations, and almost certainly cash-out,” the researchers famous. “Anybody who already has access to compromised environments can use BlackCat’s samples to infect a goal.”
As soon as executed, the malware will get the Windows system’s MachineGuid from the registry — a one of a kind crucial produced for the duration of the installation of the operating system — as properly as its UUID, just before proceeding to bypass Consumer Account Regulate (UAC), delete shadow backups, and get started the encryption method.
“This use of a modified Fendr, also recognized as ExMatter, represents a new knowledge level connecting BlackCat with past BlackMatter exercise,” the researchers mentioned.
“The modification of this reused device demonstrates a more innovative organizing and advancement routine for adapting requirements to goal environments, attribute of a maturing criminal organization.”
Identified this report attention-grabbing? Abide by THN on Facebook, Twitter and LinkedIn to read extra special content we post.
Some sections of this posting are sourced from:
thehackernews.com




 Northern Ireland TrustFord Sites Hit by Ransomware Gang
Northern Ireland TrustFord Sites Hit by Ransomware Gang