IBM has mounted a large-severity security vulnerability influencing its Cloud Databases (ICD) for PostgreSQL products that could be perhaps exploited to tamper with interior repositories and run unauthorized code.
The privilege escalation flaw (CVSS rating: 8.8), dubbed “Hell’s Keychain” by cloud security agency Wiz, has been explained as a “very first-of-its-variety offer-chain attack vector impacting a cloud provider’s infrastructure.”
Productive exploitation of the bug could allow a destructive actor to remotely execute in customers’ environments and even go through or modify knowledge stored in the PostgreSQL databases.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

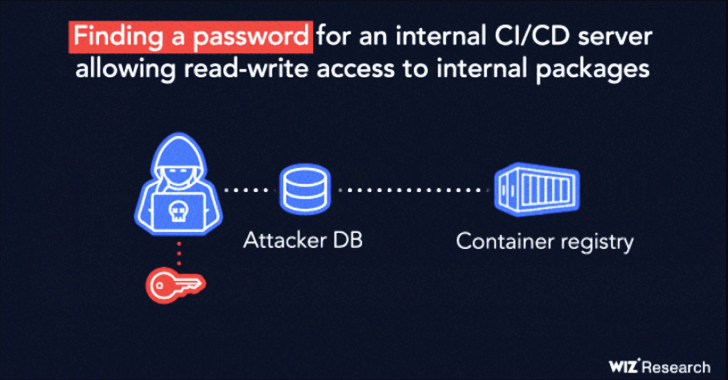
“The vulnerability is made up of a chain of a few exposed secrets (Kubernetes service account token, personal container registry password, CI/CD server credentials) coupled with extremely permissive network accessibility to inside make servers,” Wiz researchers Ronen Shustin and Shir Tamari claimed.
Hell’s Keychain commences with an SQL injection flaw in ICD that grants an attacker superuser (aka “ibm”) privileges, which is then utilized to execute arbitrary commands on the underlying digital device hosting the database instance.
This ability is weaponized to access a Kubernetes API token file, letting for broader submit-exploitation endeavours that require pulling container images from IBM’s non-public container registry, which outlets pictures associated to ICD for PostgreSQL, and scanning these photographs for extra secrets and techniques.

“Container visuals usually maintain proprietary resource code and binary artifacts that are the firm’s intellectual property,” the scientists explained. “They can also have information that an attacker could leverage to come across extra vulnerabilities and execute lateral movement within just the service’s inner natural environment.”
Wiz claimed it was able to extract interior artifact repository and FTP qualifications from the graphic manifest data files, successfully permitting unfettered read through-compose access to trustworthy repositories and IBM create servers.
An attack these types of as this could have critical ramifications, as it enables the adversary to overwrite arbitrary documents that are made use of in the establish system of the PostgreSQL graphic, which would then be set up on just about every databases instance.
The American technology large, in an impartial advisory, mentioned that all IBM Cloud Databases for PostgreSQL situations ended up most likely impacted by the bug, but noted that it identified no evidence of malicious activity.
It additional said that the fixes have been automatically utilized to consumer situations and that no additional action is essential. The mitigations were rolled out on August 22 and September 3, 2022.
“These vulnerabilities could have been exploited by a destructive actor as part of an intensive exploit chain culminating in a supply-chain attack on the platform,” the researchers explained.
To mitigate such threats, it’s suggested that businesses check their cloud environments for scattered credentials, implement network controls to avert entry to creation servers, and safeguard in opposition to container registry scraping.
Found this short article fascinating? Follow us on Twitter and LinkedIn to study much more special content we put up.
Some pieces of this short article are sourced from:
thehackernews.com

 Hackers Exploiting Redis Vulnerability to Deploy New Redigo Malware on Servers
Hackers Exploiting Redis Vulnerability to Deploy New Redigo Malware on Servers