The lately identified Linux-Based mostly ransomware strain known as Cheerscrypt has been attributed to a Chinese cyber espionage group recognised for functioning brief-lived ransomware schemes.
Cybersecurity organization Sygnia attributed the attacks to a danger actor it tracks beneath the title Emperor Dragonfly, which is also identified as Bronze Starlight (Secureworks) and DEV-0401 (Microsoft).
“Emperor Dragonfly deployed open up supply resources that had been written by Chinese developers for Chinese end users,” the enterprise mentioned in a report shared with The Hacker Information. “This reinforces promises that the ‘Emperor Dragonfly’ ransomware operators are dependent in China.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

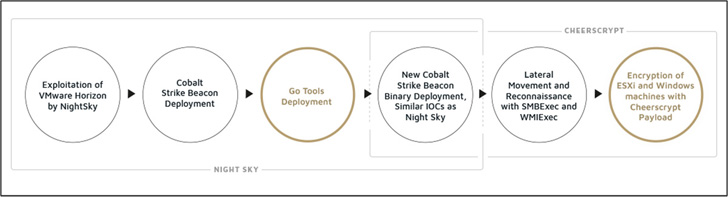
The use of Cheerscrypt is the latest addition to a very long checklist of ransomware households beforehand deployed by the team in minimal over a calendar year, which includes LockFile, Atom Silo, Rook, Evening Sky, Pandora, and LockBit 2..
Secureworks, in its profile of the group, mentioned “it is plausible that Bronze Starlight deploys ransomware as a smokescreen fairly than for money get, with the fundamental drive of thieving mental home theft or conducting espionage.”
Cheerscrypt was very first documented by Craze Micro in Could 2022, contacting out its qualities to target VMware ESXi servers as portion of a attempted-and-tested tactic known as double extortion to coerce its victims into having to pay the ransom or risk struggling with knowledge publicity.
It has also claimed to be pro-Ukrainian, displaying a “Glory to Ukraine!” concept on their dark web details leak web-site.
Curiously, the ransomware shares overlaps with the Linux version of the Babuk ransomware, which had its supply code leaked in September 2021 and also sorts the basis of Emperor Dragonfly’s Rook, Night Sky, and Pandora family members.
The threat actor’s modus operandi further more stands out for its managing of all stages of the ransomware attack lifecycle, appropriate from first entry to ransomware deployment, with out relying on affiliates and access brokers. Microsoft known as it a “lone wolf.”

Infection chains noticed to date have produced use of the critical Log4Shell vulnerability in Apache Log4j library to compromise VMware Horizon servers to fall a PowerShell payload capable of providing an encrypted Cobalt Strike beacon.
Sygnia claimed that it also uncovered a few extra Go-centered tools deployed in tandem to the beacon: a keylogger that exports the recorded keystrokes to Alibaba Cloud, an internet proxy utility referred to as iox, and a tunneling program regarded as NPS.
Cheerscrypt’s hyperlinks to Emperor Dragonfly similarities in initial access vectors, lateral movement methods, and the deployment of the encrypted Cobalt Strike beacon by way of DLL side-loading.
“Emperor Dragonfly is a China-based ransomware operator, generating it a rarity in today’s danger landscape,” researchers stated, including “a one risk actor executed the whole operation.”
Observed this report interesting? Comply with THN on Facebook, Twitter and LinkedIn to study more unique material we post.
Some sections of this report are sourced from:
thehackernews.com

 ‘Systemic ID problems for 10 million Australians’ after Optus breach, warns minister
‘Systemic ID problems for 10 million Australians’ after Optus breach, warns minister