The infamous Conti ransomware gang, which previous thirty day period staged an attack on Costa Rican administrative devices, has threatened to “overthrow” the new govt of the country.
“We are decided to overthrow the government by indicates of a cyber attack, we have currently demonstrated you all the strength and power,” the group explained on its formal internet site. “We have our insiders in your authorities. We are also doing the job on getting entry to your other systems, you have no other possibilities but to shell out us.”
In a even further attempt to raise tension, the Russian-talking cybercrime syndicate has raised its ransom demand to $20 million in return for a decryption vital to unlock their systems.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
A different concept posted on its dark web portal over the weekend issued a warning stating it will delete the decryption keys in a week, a go that would make it not possible for Costa Rica to recuperate accessibility to the data files encrypted by the ransomware.
“I attraction to each and every resident of Costa Rica, go to your governing administration and manage rallies so that they would fork out us as quickly as feasible if your latest govt cannot stabilize the problem? Perhaps it truly is value modifying it?,” the message read through.
The devastating attack, which took location on April 19, has brought about the new government to declare a point out of unexpected emergency, even though the group has leaked troves of facts stolen from the infected programs prior to encryption.
Conti attributed the intrusion to an affiliate actor dubbed “UNC1756,” mimicking the moniker menace intelligence organization Mandiant assigns to uncategorized threat groups.
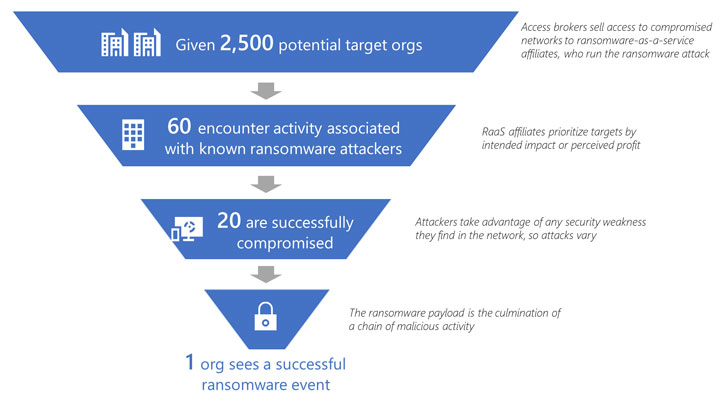
Affiliate marketers are hacking groups who hire access to currently-formulated ransomware tools to orchestrate intrusions into company networks as element of what’s called a ransomware-as-a-assistance (RaaS) gig economy, and then split the earnings with the operators.
Connected to a risk actor regarded as Gold Ulrick (aka Grim Spider or UNC1878), Conti has continued to focus on entities across the world despite suffering a enormous facts leak of its possess earlier this calendar year in the wake of its general public support to Russia in the country’s ongoing war versus Ukraine.
Microsoft’s security division, which tracks the cybercriminal team under the cluster DEV-0193, named Conti the “most prolific ransomware-involved cybercriminal exercise group lively today.”

“DEV-0193’s actions and use of the cybercriminal gig financial system means they typically add new associates and initiatives and use contractors to execute different pieces of their intrusions,” Microsoft Danger Intelligence Centre (MSTIC) reported.
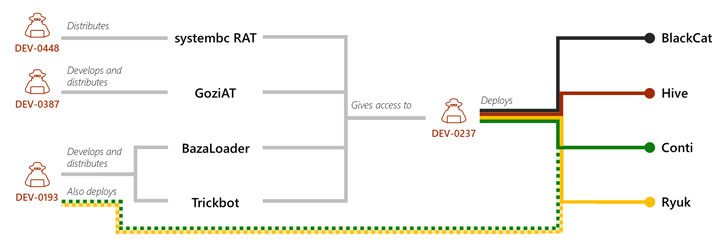
“As other malware functions have shut down for many reasons, which include authorized steps, DEV-0193 has employed builders from these groups. Most notable are the acquisitions of builders from Emotet, Qakbot, and IcedID, bringing them to the DEV-0193 umbrella.”
The interminable attacks have also led the U.S. Condition Section to announce rewards of up to $10 million for any information and facts top to the identification of crucial people today who are component of the cybercrime cartel.
Discovered this report intriguing? Adhere to THN on Fb, Twitter and LinkedIn to browse far more distinctive information we submit.
Some elements of this report are sourced from:
thehackernews.com

 Ransomware Hits American Healthcare Company Omnicell
Ransomware Hits American Healthcare Company Omnicell