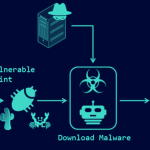
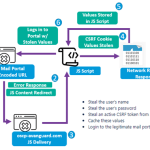
A piece of new details-thieving malware named OpcJacker has been spotted in the wild considering the fact that the next half of 2022 as element of a malvertising campaign. "OpcJacker's key functions …
Crypto-Stealing OpcJacker Malware Targets Users with Fake VPN ServiceRead More