Cybersecurity scientists have disclosed an unpatched security vulnerability that could pose a major risk to IoT goods.
The issue, which was originally described in September 2021, affects the Area Name Technique (DNS) implementation of two common C libraries identified as uClibc and uClibc-ng that are utilised for creating embedded Linux programs.
uClibc is recognized to be used by significant suppliers these kinds of as Linksys, Netgear, and Axis, as perfectly as Linux distributions like Embedded Gentoo, most likely exposing thousands and thousands of IoT units to security threats.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
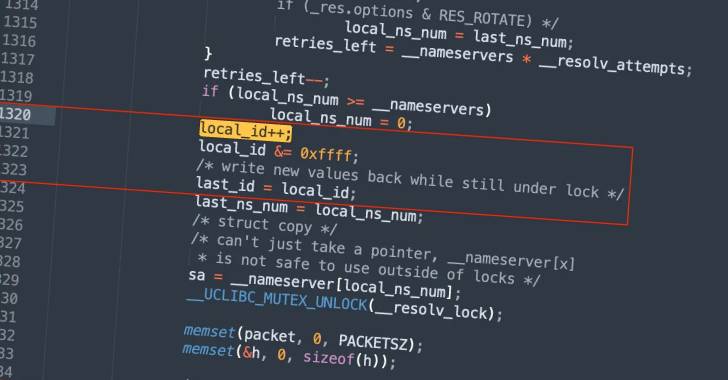
“The flaw is caused by the predictability of transaction IDs incorporated in the DNS requests generated by the library, which may perhaps make it possible for attackers to execute DNS poisoning attacks versus the target unit,” Giannis Tsaraias and Andrea Palanca of Nozomi Networks mentioned in a Monday compose-up.
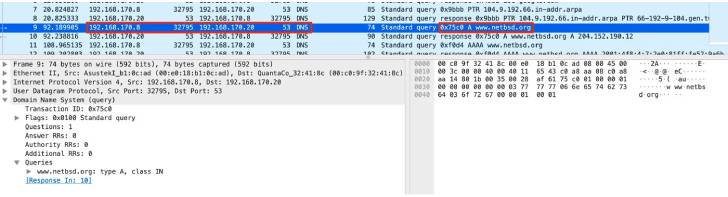
DNS poisoning, also referred to as DNS spoofing, is the method of corrupting a DNS resolver cache — which provides consumers with the IP handle connected with a domain identify — with the objective of redirecting customers to destructive web sites.

Effective exploitation of the bug could let an adversary to have out Gentleman-in-the-Center (MitM) attacks and corrupt the DNS cache, properly rerouting internet website traffic to a server under their manage.
Nozomi Networks cautioned that the vulnerability could be trivially exploited in a trusted manner should the working process be configured to use a mounted or predictable resource port.
“The attacker could then steal and/or manipulate facts transmitted by users, and accomplish other attacks from all those products to entirely compromise them,” the researchers mentioned.
Identified this posting fascinating? Comply with THN on Facebook, Twitter and LinkedIn to browse far more distinctive information we write-up.
Some elements of this write-up are sourced from:
thehackernews.com

 New Hacker Group Pursuing Corporate Employees Focused on Mergers and Acquisitions
New Hacker Group Pursuing Corporate Employees Focused on Mergers and Acquisitions